Nextcloud Letsencrypt su Raspberry Pi 4
Guida su come installare Nextcloud con Letsencrypt su Raspberry Pi 4, utilizzando Raspberry Pi OS Buster. A differenza della guida precedente, dove utilizzavo Owncloud ed apache2 come web server, adesso utilizzerò Nextcloud ed nginx.
Prerequisiti ed info
- Raspberry Pi 4/3
- Raspberry Pi OS Buster già installato ed accesso ssh
- Il raspberry dovrà avere come dominio/hostname l’equivalente di example.com. Questo può essere modificato in /etc/hostname e poi riavviare.
- Il vostro ip pubblico dovrà puntare quindi al dominio, nel caso non si avesse un ip pubblico, utilizzare un servizio di DNS.
- Assicurarsi prima, di aprire la porte 80 verso il proprio server, altrimenti non si potranno ottenere i certificati. Successivamente bisognerà aprire la 8443.
- La guida è stata testata su una installazione pulita di Raspberry Pi OS Lite.
1) Accedere al Raspberry via ssh ed Installazione Nginx web server:
$ sudo su $ su - # apt install nginx -y # systemctl start nginx # systemctl enable nginx
verifica nginx:
# systemctl status nginx
2) Installazione php7.3
# apt install -y php7.3-gd php7.3-json php7.3-mysql php7.3-curl php7.3-intl php-imagick php7.3-zip php7.3-xml php7.3-mbstring php7.3-fpm php7.3-mysql php7.3-bz2 php7.3-bcmath php7.3-gmp
modifica di 2 php.ini
# nano /etc/php/7.3/fpm/php.ini # nano /etc/php/7.3/cli/php.ini
in entrambi i files andiamo a decommentare e ad aggiornare:
date.timezone = Europe/Rome
salavare ed uscire e passare alla modifica di www.cond
# nano /etc/php/7.3/fpm/pool.d/www.conf
e decommentare le righe come sotto:
env[HOSTNAME] = $HOSTNAME env[PATH] = /usr/local/bin:/usr/bin:/bin env[TMP] = /tmp env[TMPDIR] = /tmp env[TEMP] = /tmp# systemctl restart php7.3-fpm # systemctl enable php7.3-fpm
3) Installazione e configurazione MariaDB Server
# apt install mariadb-server -y
settare password root MariaDB
# mysql_secure_installationEnter current password for root (enter for none): Press Enter Set root password? [Y/n] Y Remove anonymous users? [Y/n] Y Disallow root login remotely? [Y/n] Y Remove test database and access to it? [Y/n] Y Reload privilege tables now? [Y/n] Y
creazione user e db per nextcloud:
# mysql -u root -p
inserire password e poi i 5 comandi sotto:
create database nextcloud_db; create user nextclouduser@localhost identified by 'IN_PASSWORD'; grant all privileges on nextcloud_db.* to nextclouduser@localhost identified by 'IN_PASSWORD'; flush privileges; exit
4) Certificato SSL Letsencrypt
# apt install certbot -y
# systemctl stop nginx
# certbot certonly --standalone -d example.com
se è andato tutto bene si otterrà:
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/example.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/example.com/privkey.pem Your cert will expire on 2021-03-07. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
5) Download Nextcloud
# apt install wget unzip zip -y # cd /var/www/ # wget -q https://download.nextcloud.com/server/releases/latest.zip # unzip latest.zip # chown -R www-data:www-data /var/www/nextcloud
6) Configurazione Virtual Host
# nano /etc/nginx/sites-available/nextcloud
ed incollare dentro, con le rispettive modifiche:
upstream php-handler {
#server 127.0.0.1:9000;
server unix:/var/run/php/php7.3-fpm.sock;
}
server {
listen 80;
listen [::]:80;
server_name example.com;
# enforce https
return 301 https://$server_name:8443$request_uri;
}
server {
listen 8443 ssl http2;
listen [::]:8443 ssl http2;
server_name example.com;
# Use Mozilla's guidelines for SSL/TLS settings
# https://mozilla.github.io/server-side-tls/ssl-config-generator/
# NOTE: some settings below might be redundant
ssl_certificate /etc/letsencrypt/live/example.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/example.com/privkey.pem;
# Add headers to serve security related headers
# Before enabling Strict-Transport-Security headers please read into this
# topic first.
#add_header Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;" always;
#
# WARNING: Only add the preload option once you read about
# the consequences in https://hstspreload.org/. This option
# will add the domain to a hardcoded list that is shipped
# in all major browsers and getting removed from this list
# could take several months.
add_header Referrer-Policy "no-referrer" always;
add_header X-Content-Type-Options "nosniff" always;
add_header X-Download-Options "noopen" always;
add_header X-Frame-Options "SAMEORIGIN" always;
add_header X-Permitted-Cross-Domain-Policies "none" always;
add_header X-Robots-Tag "none" always;
add_header X-XSS-Protection "1; mode=block" always;
# Remove X-Powered-By, which is an information leak
fastcgi_hide_header X-Powered-By;
# Path to the root of your installation
root /var/www/nextcloud;
location = /robots.txt {
allow all;
log_not_found off;
access_log off;
}
# The following 2 rules are only needed for the user_webfinger app.
# Uncomment it if you're planning to use this app.
#rewrite ^/.well-known/host-meta /public.php?service=host-meta last;
#rewrite ^/.well-known/host-meta.json /public.php?service=host-meta-json last;
# The following rule is only needed for the Social app.
# Uncomment it if you're planning to use this app.
#rewrite ^/.well-known/webfinger /public.php?service=webfinger last;
location = /.well-known/carddav {
return 301 $scheme://$host:$server_port/remote.php/dav;
}
location = /.well-known/caldav {
return 301 $scheme://$host:$server_port/remote.php/dav;
}
# set max upload size
client_max_body_size 512M;
fastcgi_buffers 64 4K;
# Enable gzip but do not remove ETag headers
gzip on;
gzip_vary on;
gzip_comp_level 4;
gzip_min_length 256;
gzip_proxied expired no-cache no-store private no_last_modified no_etag auth;
gzip_types application/atom+xml application/javascript application/json application/ld+json application/manifest+json application/rss+xml application/vnd.geo+json application/vnd.ms-fontobject application/x-font-ttf application/x-web-app-manifest+json application/xhtml+xml application/xml font/opentype image/bmp image/svg+xml image/x-icon text/cache-manifest text/css text/plain text/vcard text/vnd.rim.location.xloc text/vtt text/x-component text/x-cross-domain-policy;
# Uncomment if your server is build with the ngx_pagespeed module
# This module is currently not supported.
#pagespeed off;
location / {
rewrite ^ /index.php;
}
location ~ ^\/(?:build|tests|config|lib|3rdparty|templates|data)\/ {
deny all;
}
location ~ ^\/(?:\.|autotest|occ|issue|indie|db_|console) {
deny all;
}
location ~ ^\/(?:index|remote|public|cron|core\/ajax\/update|status|ocs\/v[12]|updater\/.+|oc[ms]-provider\/.+)\.php(?:$|\/) {
fastcgi_split_path_info ^(.+?\.php)(\/.*|)$;
set $path_info $fastcgi_path_info;
try_files $fastcgi_script_name =404;
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param PATH_INFO $path_info;
fastcgi_param HTTPS on;
# Avoid sending the security headers twice
fastcgi_param modHeadersAvailable true;
# Enable pretty urls
fastcgi_param front_controller_active true;
fastcgi_pass php-handler;
fastcgi_intercept_errors on;
fastcgi_request_buffering off;
}
location ~ ^\/(?:updater|oc[ms]-provider)(?:$|\/) {
try_files $uri/ =404;
index index.php;
}
# Adding the cache control header for js, css and map files
# Make sure it is BELOW the PHP block
location ~ \.(?:css|js|woff2?|svg|gif|map)$ {
try_files $uri /index.php$request_uri;
add_header Cache-Control "public, max-age=15778463";
# Add headers to serve security related headers (It is intended to
# have those duplicated to the ones above)
# Before enabling Strict-Transport-Security headers please read into
# this topic first.
#add_header Strict-Transport-Security "max-age=15768000; includeSubDomains; preload;" always;
#
# WARNING: Only add the preload option once you read about
# the consequences in https://hstspreload.org/. This option
# will add the domain to a hardcoded list that is shipped
# in all major browsers and getting removed from this list
# could take several months.
add_header Referrer-Policy "no-referrer" always;
add_header X-Content-Type-Options "nosniff" always;
add_header X-Download-Options "noopen" always;
add_header X-Frame-Options "SAMEORIGIN" always;
add_header X-Permitted-Cross-Domain-Policies "none" always;
add_header X-Robots-Tag "none" always;
add_header X-XSS-Protection "1; mode=block" always;
# Optional: Don't log access to assets
access_log off;
}
location ~ \.(?:png|html|ttf|ico|jpg|jpeg|bcmap)$ {
try_files $uri /index.php$request_uri;
# Optional: Don't log access to other assets
access_log off;
}
}
salvare ed uscire. Poi fare un paio di modifiche:
# ln -s /etc/nginx/sites-available/nextcloud /etc/nginx/sites-enabled/ # nano /etc/nginx/nginx.conf
e decommentare la linea sotto:
server_names_hash_bucket_size 64;
fare un test di nginx:
# nginx -t
se non ci sono errori avremo un output come sotto:
root@example:/var/www# nginx -t nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful# systemctl restart nginx # systemctl restart php7.3-fpm
7) Nextcloud post installazione

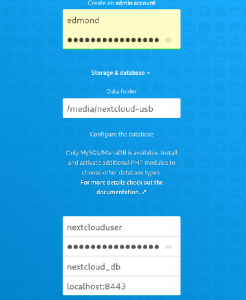 andare all’indirizzo del server:
andare all’indirizzo del server:
# hostname -I
creare username e password per l’accesso via web, e poi inserire nextclouduser e nextcloud_db. Nel caso di porta diversa della 443, è meglio inserirla come in figura sopra. I dati di default saranno in /var/www/nextcloud/data. Ma conviene sempre tenerli all’esterno della sd-card. Esempio con usb esterna.
8) Creazione della cartella di storage e relativi permessi:
# mkdir /media/nextcloud-usb
# groupadd www-data
# usermod -a -G www-data www-data
# chown -R www-data:www-data /media/nextcloud-usb
# chmod -R 775 /media/nextcloud-usb
adesso abbiamo bisogno di conoscere UUID del disco usb e configurare /etc/fstab per il montaggio automatico:
# blkid
# nano /etc/fstab
ed aggiungere qualcosa del genere in /etc/fstab:
UUID=f9kjhg70-0784-4eaa-9cc5-4ctrewc62275 /media/nextcloud-usb ext4 defaults 0
# reboot
al riavvio verificare se la usb esterna è stata montata correttamente:
$ df -h
Questa guida consente di avere un server cloud personale, ma bisogna ricordarsi che bisognerà proteggerlo, e quindi integrare delle robuste policy di sicurezza, come fail2ban, iptables, ufw, ecc ecc.
Nextcloud Letsencrypt su Raspberry Pi 4
enjoy 😉